What is Port Security? Port Security allows you to restrict what devices can be connected to a Switch Port. You have three options (modes) for how to deal with unpermitted devices. Lets run through these options below.
As for where you might use this. It would be a good idea to use this configuration in meeting rooms if you didn’t want guests to be able to plugin to the network.
If you have issues with staff moving equipment around themselves then setting the sticky option, and Violation to Restrict would mean their equipment wouldn’t work until they’d moved back to their previous desk.
Configuration
The Basic configuration for Port Security is as below:-
1 - Interface Gi0/0 <CR>
2 - Switchport Port-Security <CR>
3 - Switchport Port-Security Mac-Address [h.h.h.h(Mac Address)|Sticky]
4 - Switchport Port-Security Maximum [1-1536]
5 - Switchport Port-Security Violation [Protect|Restrict|Shutdown]If we start by looking at Line 3, Here we can either Hardcode Mac addresses against the port, Or we can enable Sticky mode whereby the switch will “Learn” the Mac Addresses as new devices are connected to the switches ports (Up to the maximum number in Line 4 (See Below)
The Maximum option configures how many Mac Addresses the switch can learn against each port where using the Sticky option.
Violation defines how the switch will deal with the Violation (Exceeded the maximum number of devices, Or (Important point) if a device has already been learnt / configured on another port, It will trigger the violation if it’s moved to another port)
Violations
So what do the three Violations mean. Well it’s easiest (for me atleast) to remember Protect and Restrict in alphabetical order as they do the same job, one just does it better then the other (Restrict).
Restrict
So to start with Restrict then, If a device has already been learnt on another port, Or if you have the maximum number of devices already configured on the port. The port will trigger the Restrict violation, It won’t allow the device to connect to the network (Port won’t come up in terms of layer 2 / 3) and if you’re watching the logs / Console a console message will be triggered.

These messages will keep being generated every few seconds until the device that’s violating these policies has been removed, or the configuration has been corrected.
Protect
So Protect works in very much the same way as Restrict, It just doesn’t tell you. No console messages, Nothing will show in logs/syslogs and so troubleshooting these violations will be more challenging as it may appear as a physical / NIC issue to start with.
Shutdown
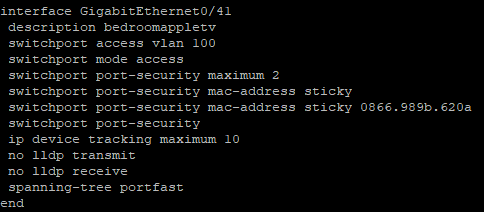
When Shutdown is configured, once the Maximum number of addresses has been configured / learnt then the switch will physically shutdown the port (Err-Disabled)
You would see this under show interfaces status err-disabled and you would need to resolve the issues and shut / no shut the port in order to bring it back up again. If you were checking syslog, or the logs at the time of the violation then you would see an error (See Below)
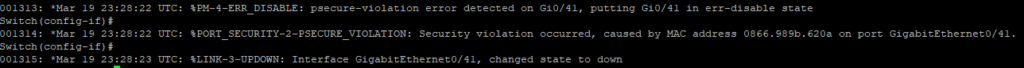
And checking Show Interfaces Status Err-Disabled shows the below violation as expected.
Show Commands
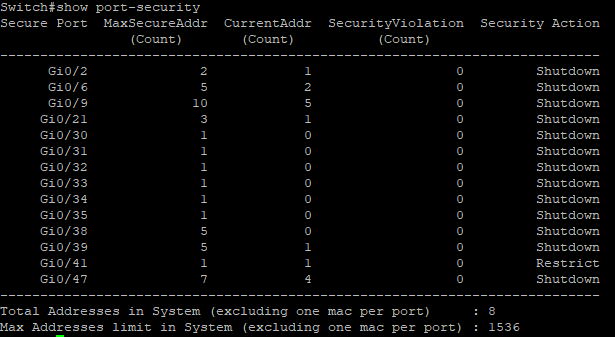
Show Port-security
This command shows all ports with Port-Security enabled, Their Violation Mode and the max/current violation counts.
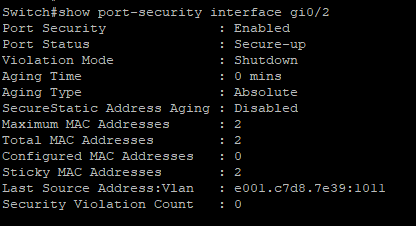
We can also hone in on an individual port by entering Show port-security interface [InterfaceName]
This shows us the same details as before, But also the Last Source Address. If you’re not using Sticky mode for learning addresses this may be useful.
Key Points
Shutdown is the Default Violation and even if typed, It does not show in configuration.
For Port-Security Configuration to apply, switch ports must be in Access mode. You cannot apply to Dynamic ports.
If a device has been learnt on one port, It cannot be unplugged and plugged into a different port, This would trigger the port Violation.
Hope you’ve found this article useful. For additional details please see Cisco’s article here If you’d like to read our other Cisco articles on this site, Click Here
