This is a guide to help with managing users mailbox rules via Powershell.
Getting Started
Some viruses / malicious actors have been known to add hidden rules in to delete emails, or potentially forward them outside of the organisation. As these are hidden there is no way for the user to see them in their Outlook. Using Powershell may also be the easiest way to remove user created mail forwards e.t.c from a user nolonger with the business, or managing out of office rules when a user is out of the office.
These have been tested on Exchange Online but will likely work for On-Premise version (2007 – 2019) also.
Start by connecting to Exchange Powershell. If you need to install the Exchange Online Powershell to do this then please follow this link for instructions.
Assuming you already have Exchange Online Powershell installed then open up a powershell prompt and type Connect-Exchangeonline. You’ll be prompted to login to your tenant.
Once you’ve logged into your tenant we can use the Get-InboxRule command to check the rules on the mailbox.
The get-inboxrule command requires either primarySMTPaddress or the Identity to identify the mailbox.
The command is get-inboxrule -mailbox <EmailAddress Of Mailbox>
The powershell window will show you the rulename, Whether it’s Enabled and the RuleIdentity
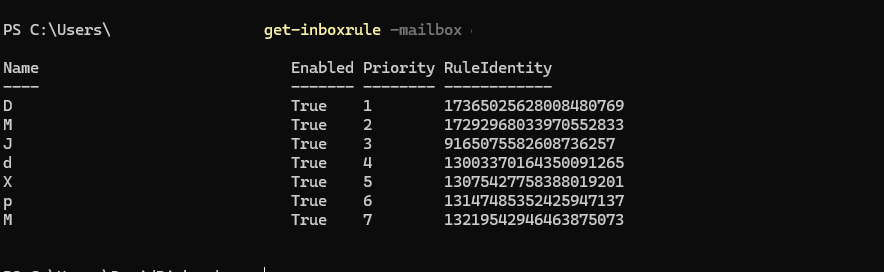
If you want to look further into one of the rules then be careful, The Identity command requires the RuleIdentity putting in DoubleQuotes (Speech Marks) or you’ll recieve an error.
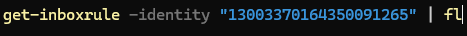
You can pipe the reply into FL (Format-List) to get all the information for the rule, but the response can be quite overwhelming. To start with I would use something similar to the below command, And work from this to add any additional columns to help you.
get-inboxrule -identity "13003370164350091265" | select Enabled, Name, Description, Inerror, DeleteMessage, ForwardTo, RedirectTo, StopProcessingRulesFurther Reading
The full command syntax for Get-InboxRule can be found by entering get-help get-inboxrule, or get-inboxrule -examples. The information contained within can also be found here
